Alice and Bob's Relationship is broken

This is an updated version of a post originally published on the JLINC blog (March 21, 2018).
Alice and Bob are the primary characters in a cast of characters first used in cryptographic circles as placeholder names to represent different parties in a transaction. The story goes like this:
Alice wants to send a message to Bob, but she doesn’t want anyone but Bob to be able to read it. Bob also doesn’t want anyone to read his messages to Alice. They do this by securely exchanging special ‘keys’ to exchange documents and data.
All well and good so far. This transaction and this representation make sense because Alice and Bob are peers. They have a common interest in having a secret communication and have the same capability – defined in cryptographic protocols. In terms of this exchange, Alice and Bob are equals. And because Alice and Bob are such a cute couple they have come to represent many other different types of transactions on the web. But when we take Alice and Bob out of the crypto context and use them as placeholders for normal web transactions, their relationship is different. There is no equality via protocol. By and large these relationships are defined by the privacy policies and terms of use of the websites that Alice visits. And these do not define a relationship between peers.
The utility of privacy policies
Privacy policies are created and published, by and large, for the purpose of reducing corporate risk. In that sense, they serve the same purpose as any warranty that you receive with any product. If you read the warranty on your latest household appliance you will probably find, after translating the legalese into English, that the company provides very little in the way of an actual guarantee. Privacy policies serve the same purpose. In a 2014 survey The Pew Research Centre asked people if having a privacy policy means that a company will keep user information confidential. The correct answer is, sadly, “FALSE”. But only 44% of respondents answered correctly. 56% of users answered “TRUE”.
Forbes found one refreshingly honest privacy policy that ended with the phrase “All your privacy are belong to us. We mean it.”

Terms of Use are similarly weighted away from Alice. These are standard form contracts or ‘contracts of adhesion’ where the terms are set by the website and Alice is effectively left with two options: take it; or leave it.
When Alice is surfing the web she is typically using sites set up by companies or organizations. When Alice visits one of these sites, she implicitly or explicitly agrees with each site’s “Terms of Use” and/or implicitly consents to their “Privacy Policy”. But unlike the key exchange between Alice and Bob, this not a relationship between equals. The top 5 most visited sites on the web are (data from Alexa):
Globally
United States
Does it really make sense to think of Google, YouTube or Facebook as Alice’s “peer” in the way that Alice and Bob are peers for exchanging cryptographic keys? Obviously not. There is a serious power imbalance between this Alice and this Bob. It would really be better to think of these relationships as between Alice and Bob Company or BobCo (or even EvilBobCo). The nature of this imbalance, combined with the dependence of these web sites on advertising for revenue, creates a natural motivation for designers to use 'dark patterns' to ensure that users stay on the sites by whatever means necessary.
As a result of this imbalance, facilitated by dark designs, BobCo is able to sell Alice’s data, or access to Alice’s web page when she is on Bob’s site, to Charlie who in turn can make Alice’s information available to as many organizations as are interested in that data. This uncontrolled trade in data and almost complete lack or respect for Alice’s privacy or Alice as a person is the basis for the current business model of the Internet and what is meant by the phrase, “If you’re not the customer, you are the product”. Thousands of companies are competing for the chance to process your data, probably unbeknownst to you.
And, by the way, individually you are not that valuable a product. In 2019, Facebook reported over $69 billion in global advertising revenue. But when calculated on a per user basis that translates to less than $30. So your entire years worth of Facebook viewing and clicking is worth $30 to Facebook. At that price, you have little or no leverage to influence any of Facebook’s policies or attitudes. You and Facebook are not equals in the relationship.
Personal Data Value Chain
So Alice and Bob are not equals. And the structure of the relationship between users and services encourages the extraction and monetization of personal data without meaningful consent. This is not a trade-off of service for a value that most people would make if they thought that they had a choice. This is the so-called “Tradeoff Fallacy”. It’s been known since at least 2009, for example, that Americans reject tailored advertising when it is explained to them. Until Alice can monitor and control what happens to her data, she cannot hold Bob accountable and the exploitation of her data will continue.
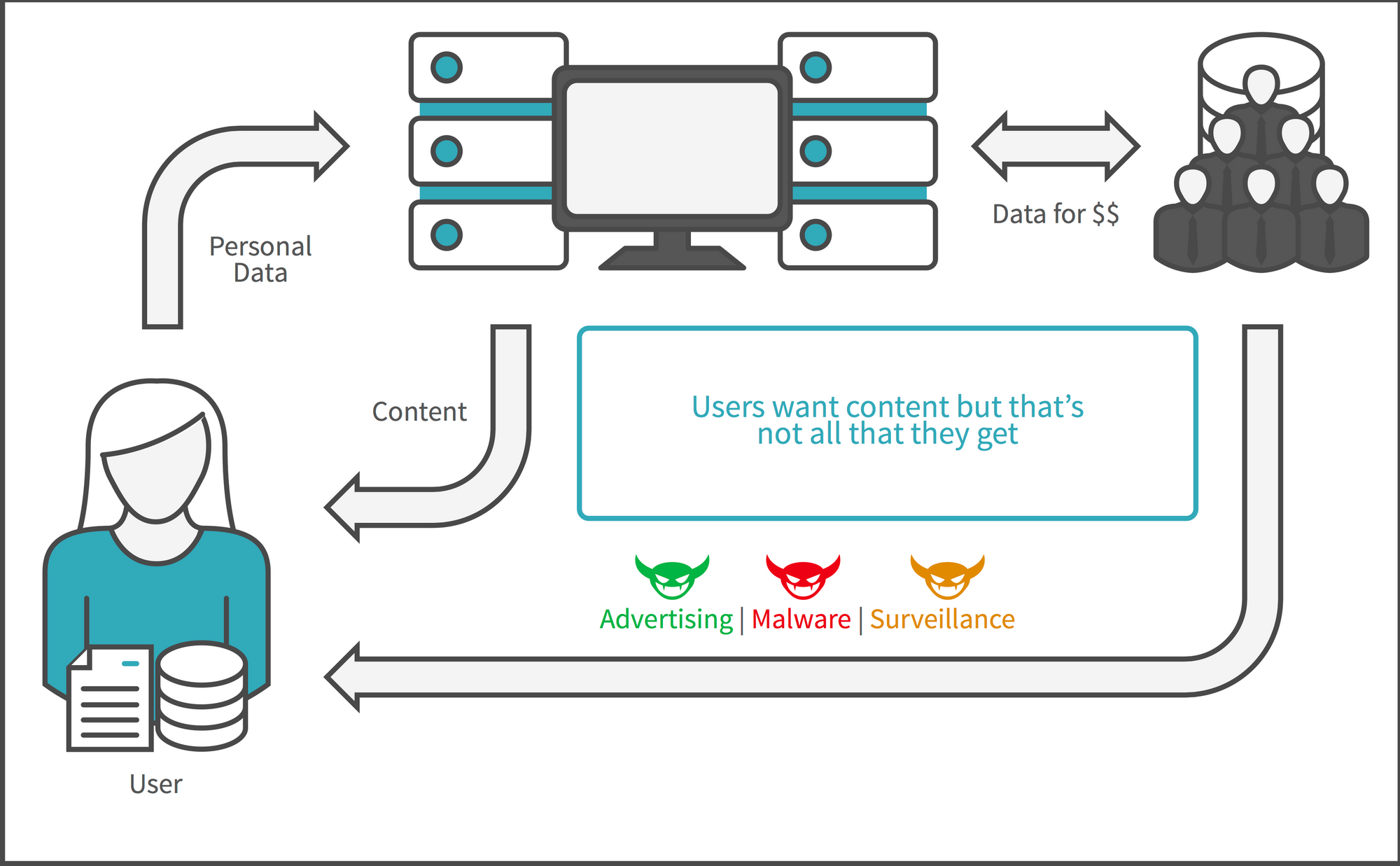
There is work being done to address this situation. In the Kantara Initiative, the User-Managed Access Work Group has released the UMA protocol extending OAuth’s capability to enable Alice to control who has access to her resources. Similarly, Kantara has produced a consent receipt specification to enable accountability and transparency in consent. The Vendor Relationship Management project (ProjectVRM) has sparked or inspired dozens of companies or initiatives to empower users in the commercial space, including the Me2B Alliance. MyData Global is an NGO dedicated to the proposition that a person should be at the centre of their own data. The JLINC protocol is an open protocol that will enable Alice to do exactly the kind of monitoring and have the kind of control over her data that is missing.
In the meantime, the next time you read about Alice and Bob, think about the context and draw your own conclusion about the nature of that relationship. Most of the time, I suspect, you will find that it is Alice and BobCo/EvilBobCo and that whether Bob is evil or not, Alice has no power.
Bob is a bully and needs to be stopped.





Member discussion